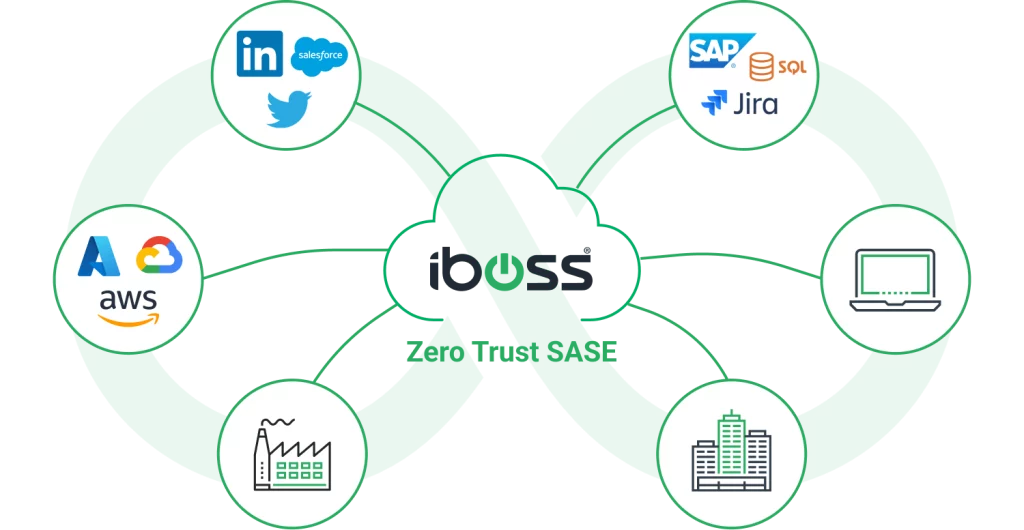
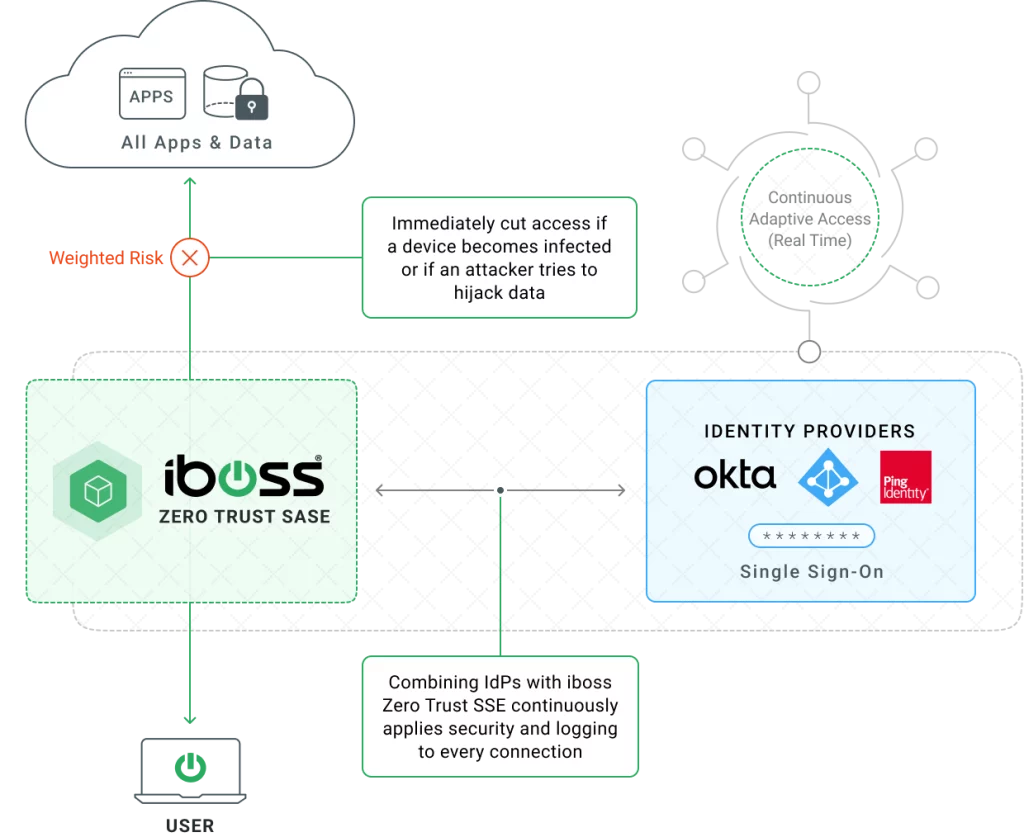
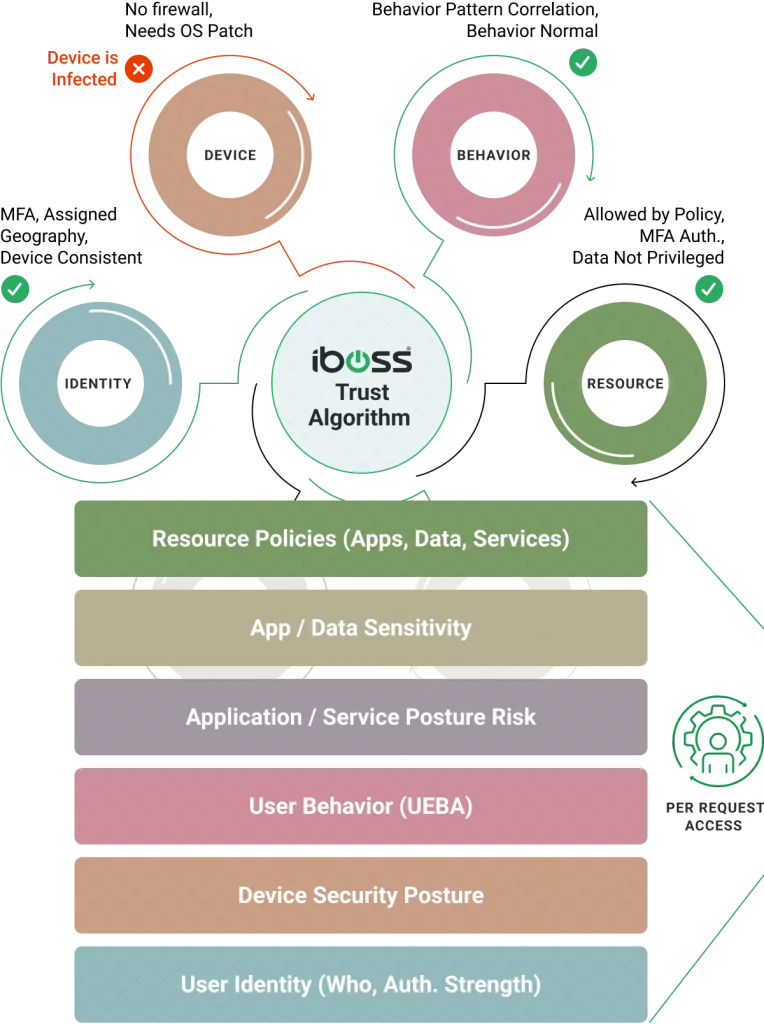
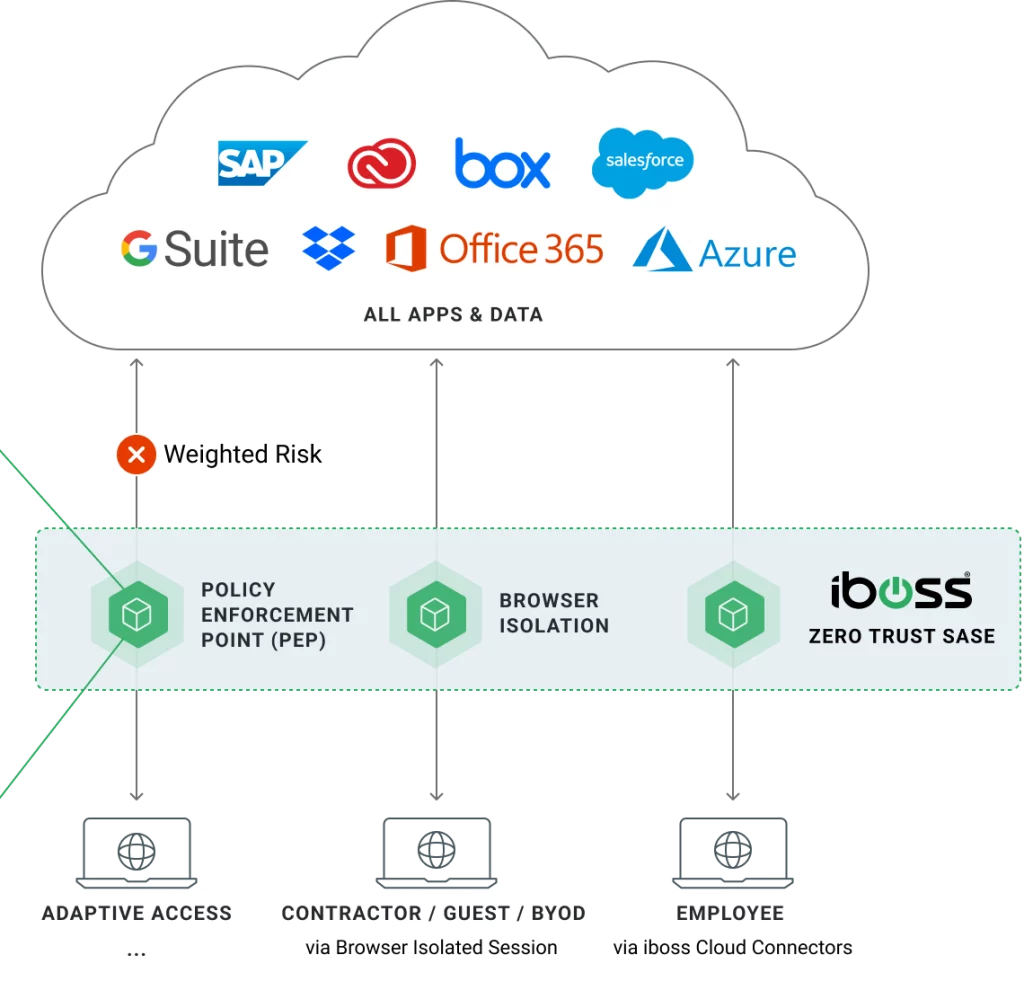
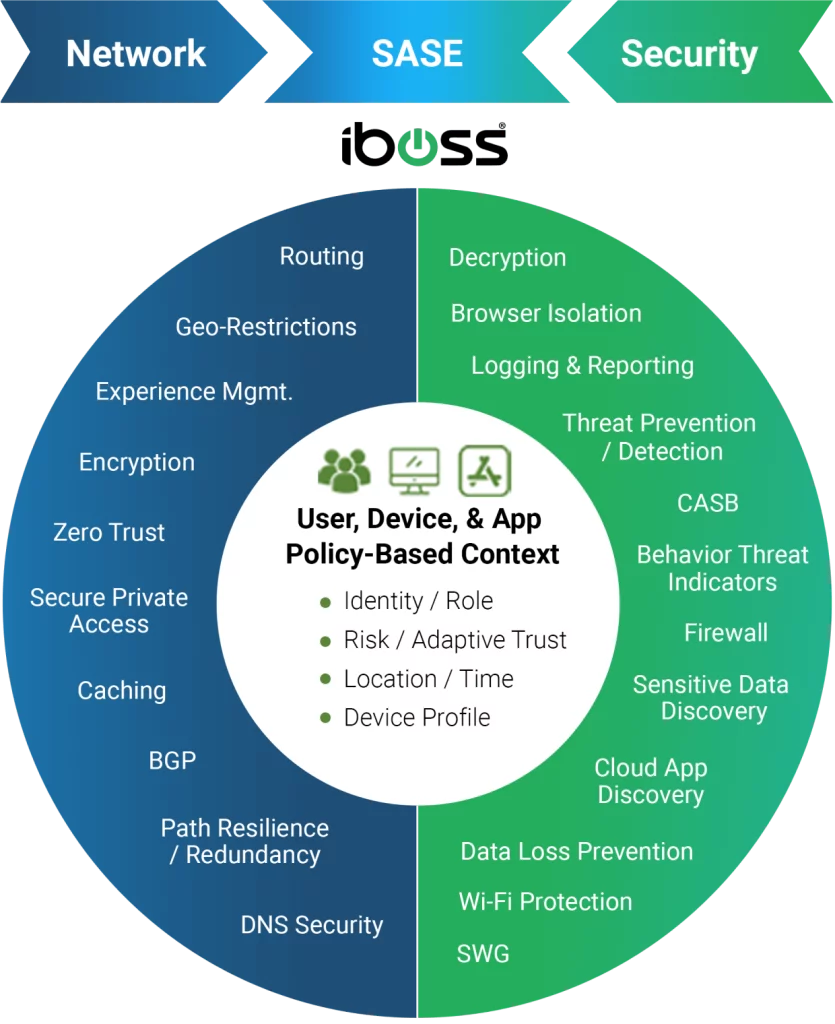
The iboss Zero Trust SASE provides a secure and easy way to connect remote users to on-prem and cloud applications. The platform uses ZTNA to provide secure access to remote users, only allowing users access to the specific resources they are authorized to access. This is more secure than a VPN, which allows remote users access to the entire enterprise network, which could lead to an increased risk of breaches and data loss.
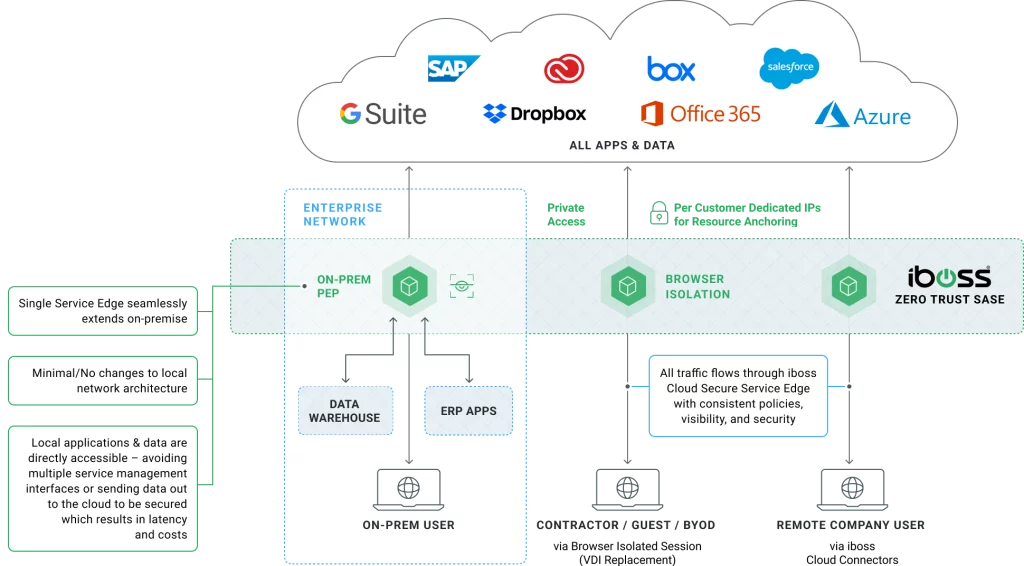
The iboss Zero Trust SASE also replaces legacy proxy appliances with Secure Access Service Edge, which provides direct connections to all applications and services, without appliances. This eliminates the worry of overloaded appliances due to the increased load from video conferencing and other services.
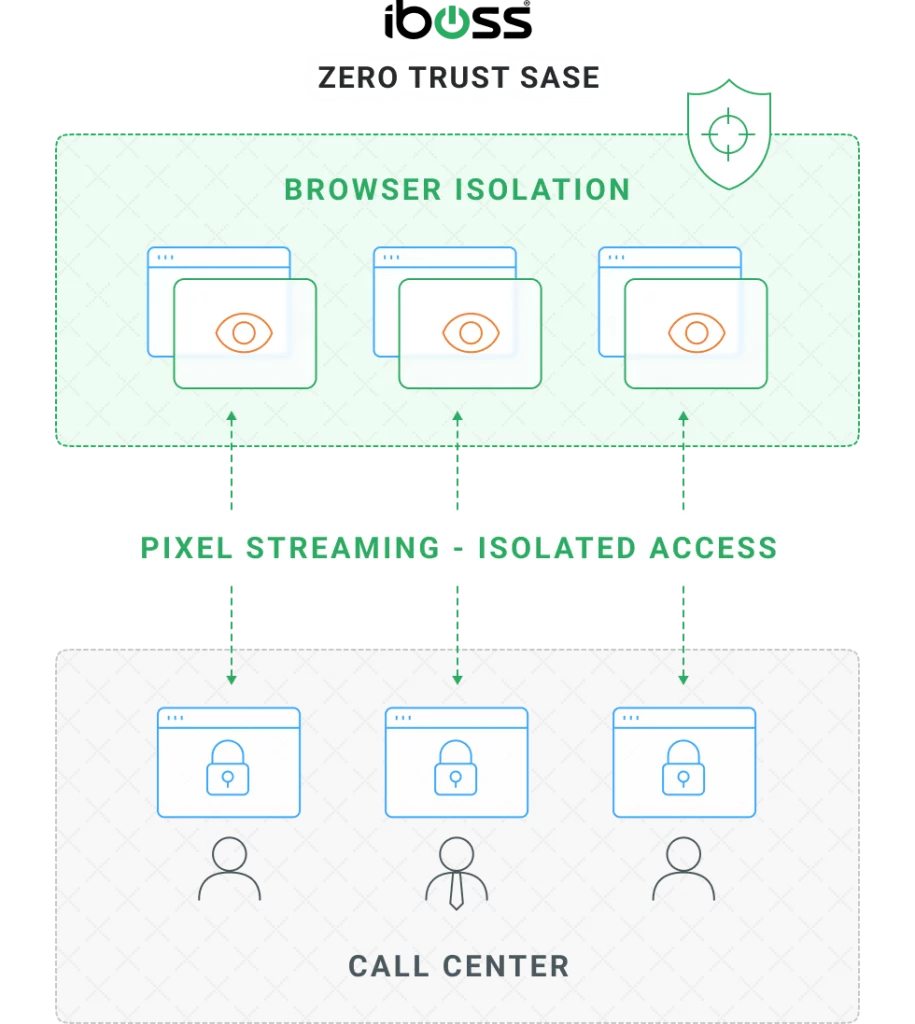
The iboss Zero Trust SASE eliminates and improves on the capabilities provided by VDI by providing isolated access to sensitive resources through a pane-of-glass delivered through the end-user’s browser. And because it’s part of a unified platform, Browser Isolation benefits from the capabilities of ZTNA and Secure Access Service Edge to provide access to private applications while applying security and logging to every request automatically.